HTB Sense Writeup
Sense is a medium level box that requires some basic knowledge of PHP and enumeration. By achieving root access on this box, I learned how to exploit PFsense by bypassing some filtering, and using a pubic exploit proof of concept.
Enumeration
First I did a nmap scan: nmap -sC -sV -oA scan 10.10.10.60. This will scan for versioning and open ports and will output the results to scan.nmap. Here’s what the results produced.

Since we see that ports 80 and 443 are open, we know the server is running an HTTP/HTTPS server. Let’s check the website:

We see a pfsense login page (which is why this box is named Sense). I tried some the normal default credits of admin:pfsense and some common user/password combinations and got no luck.
Next, I use dirbuster to potentially find any directories and files within the webserver. I start off with the common.txt wordlist. And here’s what it outputted
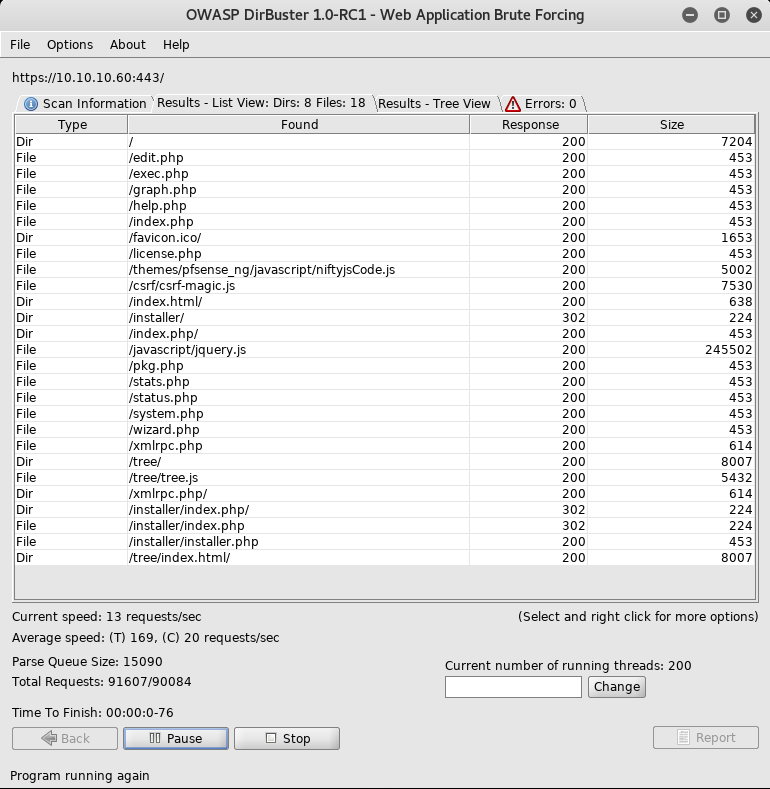
After checking through each of the files for awhile, I couldn’t find any useful information. I decide to use another wordlist with additional extensions: txt, html, jpeg (on dirbuster near the lower right there’s a File extension box, you can add extensions by separating them with a comma).
Here are the results:

There are couple interesting files: changelog.txt and system-users.txt.
Here’s what the changelog.txt file says:

So in this txt file we see only 2 out of 3 vulnerabilities were patched… Interesting
Here’s what the system-users.txt file says:

Exploitation
So we have some information about an unpatched vulnerability within pfsense that the firewall failed to update.
Doing some research and googling pfsense vulnerabilities, I come across this page that lists published vulnerabilities within pfsense
So with the hint we were given about 2 out of 3 vulnerabilities, I assume the most recent one from 2019 wasn’t accounted for as this could be an older box or version.
Reading through each of the vulnerabilities, CVE-2016-10709 seemed the most likely to work. Reading through the exploit-db, this is how they described the vulnerability
So we see that as an non admin user, we can remotely execute code as root.
From the hint earlier, we know there was a ticket for an account Rohit to be made with default passwords. Testing on the main webpage, I figured out the user:pass is rohit:pfsense. (note: it has to be lower case ‘r’ for whatever reason and I was stuck on this for longer that I should have been).
Reading back on the cvedetails page linked above, I read there’s a rapid7 link along with information about a metasploit module we can use.
The metasploit module: exploit/unix/http/pfsense_graph_injection_exec.
With the information we have gathered, we can run this metasploit module. Here’s a picture of me running the metasploit module and configuring the settings:

Running the exploit, we get a meterpreter session! Doing a whoami check reveals we are root!

Flags:
User: /home/rohit/user.txt
Root: /root/root.txt
Last updated