HTB Grandpa Writeup
This HackTheBox machine is related to a previous HackTheBox machine: Granny. By achieving root on this box, I learned about exploiting a related CVE that was widely used when released.
Enumeration
Starting off with a basic enumeration scan: nmap -sC -sV -oA granny 10.10.10.14. Here’s the result:

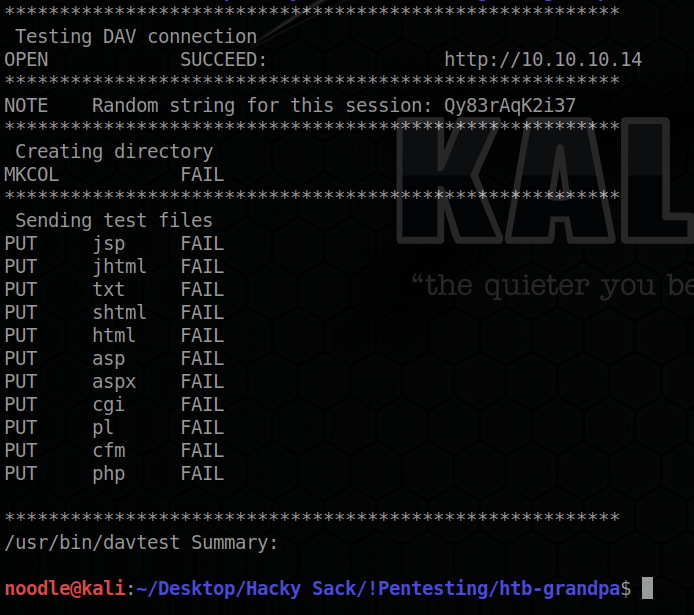
We see that port 80 is open that’s hosting an IIS webserver. Doing a previous challenge Granny I learned about WebDAV and this box also seems to have some WebDAV funcitonality. I do a similar davtest scan. Here’s the result:
Meanwhile, in the background, I run a gobuster script to see if there’s any additional directories. The command I did was gobuster dir -u http://10.10.10.14 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt. And this is what it found:
Status: 403 means we don’t have access to that directory, Status: 301 is a URL redirection, but we can access it.
So basically from our findings, we see the only open port is 80 with WebDAV. But with this WebDAV (unlike HackTheBox grandma), we cannot upload files so we can’t upload an .asp file to execute and get a reverse shell.
I decided to do some googling:

The first link by Rapid7 shows the module exploit/windows/iis/iis_webdav_scstoragepathfromurl.
Exploitation
Using the module, configuring the settings, then later executing the exploit, we get a meterpreter shell.

In meterpreter, I do shell to get a native windows shell. Doing a whoami check outputs nt authority\network service. This isn’t the administrator account.
Next, something I learned by doing this HackTheBox challenge is to migrate processes to a different process that you own or a process that’s the same architecture as your exploit/payload. So for this challenge, I migrate to a process that I own (as nt authority\network service.
*NOTE: When doing this challenge, the meterpreter session kept closing randomly. I think it’s due to the process that I migrated to so I suggest trying a different process if possible.

Privesc
First step I do is to use a metasploit module that will collect a list of known exploits based on the system information you have on the machine and then suggests you a list of exploits that may work.
Trying the first exploit listed (exploit/windows/local/ms10_015_kitrap0d) that “appears to be vulnerable” by ended up crashing the box so that didn’t work.
Trying the second exploit (exploit/windows/local/ms14_070_tcpip_ioctl) that “appears to be vulnerable” by ended up getting me a shell:

Getting Root/User flags
Eventually I wander into this directory that contains an Administrator directory and a Harry directory that looks to be a user on the box.

Checking the Desktop inside each of those reveals the Root flag and the User flag
Flags
Root: C:\Documents and Settings\Administrator\Desktop\root.txt
User: C:\Documents and Settings\Harry\Desktop\user.txt
Sources
Last updated